Setting Up an Amazon AWS Account
If you do not have an Amazon AWS account, you can sign up for one easily at http://aws.amazon.com/. Then you can get started using AWS for load testing with RedLine13.
Signing up is free and you will only pay for the services that are used. As an example, if you do a load test of 50,000 users for an hour the approximate cost is $2.00 and would be charged to your account on Amazon. There is no fee from RedLine13.
AWS Identity and Access Management (IAM) Setup Instructions
There are 2 ways to upload AWS credentials. The Cross Account Role method, described below, is the preferred method. The alternative is the Key/Secret method. The steps below are detailed with screenshots so that you can be sure you get it right.
You can also view this detailed video demonstrating how to link AWS with RedLine13 in addition to step-by-step guide’s.
- Login to the AWS IAM console at https://console.aws.amazon.com/iam/home.
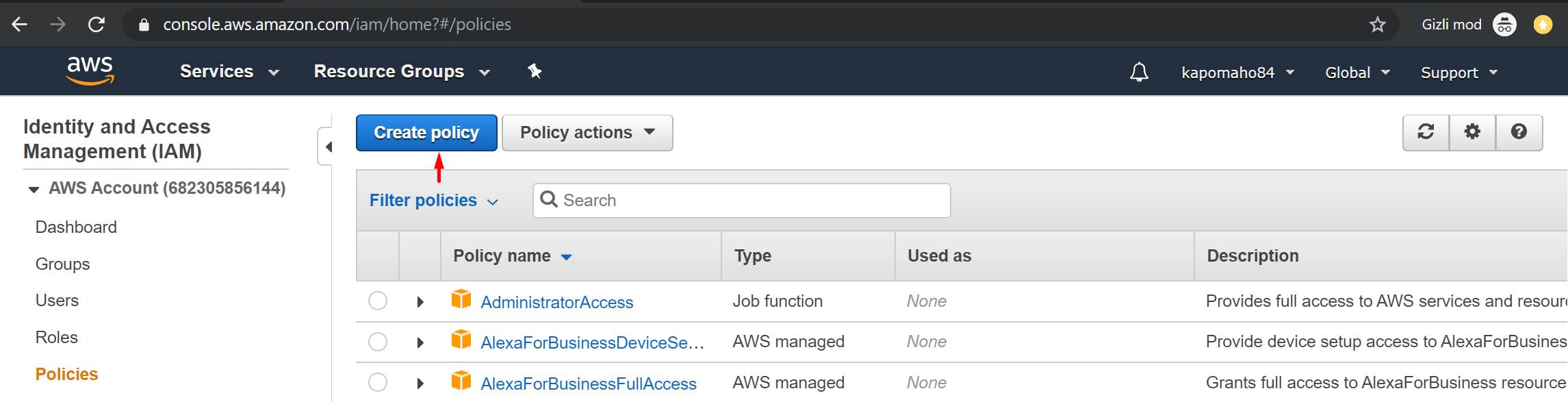
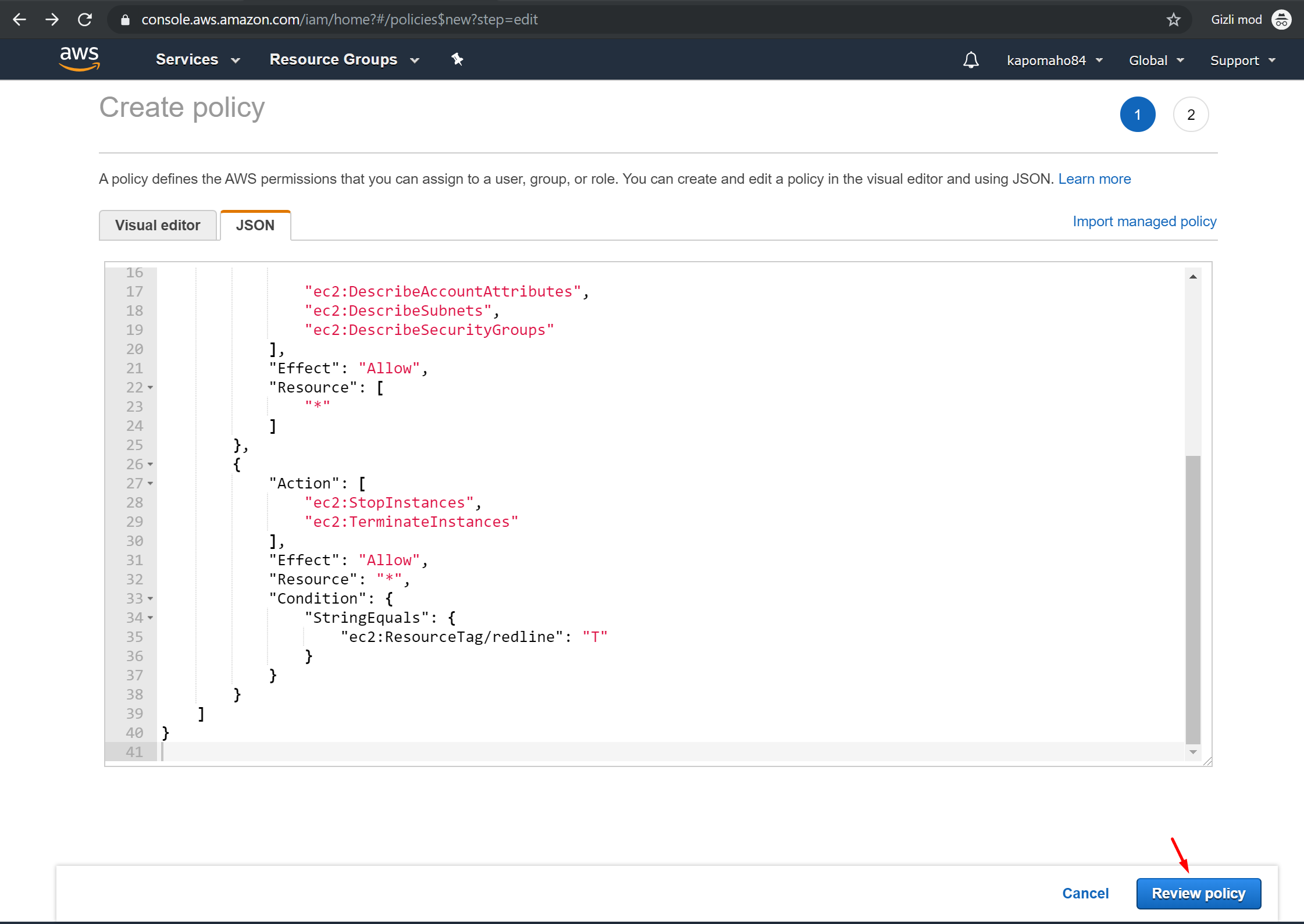
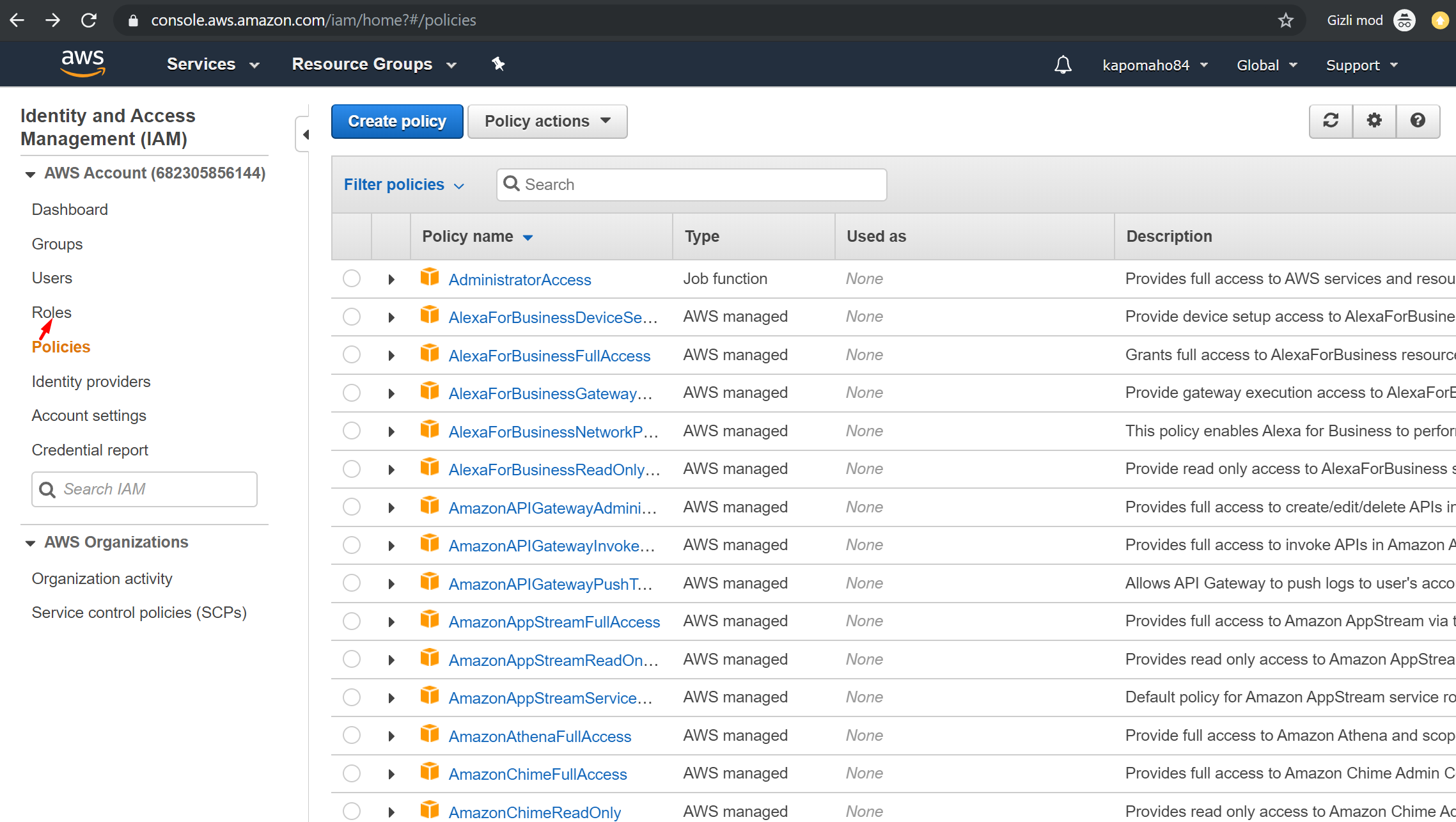
- Click the “Policies” link, then the “Create Policy” button.
Select the “JSON” tab, then paste the following Policy JSON document.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"iam:GetUser",
"iam:SimulatePrincipalPolicy",
"iam:PassRole",
"iam:CreateServiceLinkedRole",
"ec2:CreateTags",
"ec2:DescribeInstances",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeSpotInstanceRequests",
"ec2:RequestSpotInstances",
"ec2:RunInstances",
"ec2:StartInstances",
"ec2:DescribeAccountAttributes",
"ec2:DescribeSubnets",
"ec2:DescribeSecurityGroups"
],
"Effect": "Allow",
"Resource": [
"*"
]
},
{
"Action": [
"ec2:StopInstances",
"ec2:TerminateInstances"
],
"Effect": "Allow",
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/redline": "T"
}
}
}
]
}
3. The iam:* actions are not required, but allow RedLine13 to validate your policy.
iam:PassRole
Used for extended security to limit termination to instance-profiles.
You will need to also change the condition for stop and terminate to specify the instance profile with privileges.
“ec2:InstanceProfile”: “arn:aws:iam::ACCOUNT:instance-profile/NAME_OF_INSTANCE_PROFILE”
SimulatePrincipalPolicy
Used to test a policy for permissions
The actions following the skipped line are not essential, but recommended.
DescribeAccountAttributes
Used to determine account settings to help us prevent you from starting servers that are incompatible with your AWS account settings
DescribeSubnets
Used to show list of subnets in a drop down
DescribeSecurityGroups
Used to show your list of security groups when creating a test
The actions in the second action step are not required, but are limited to only resources tagged with the RedLine13tag.
StopInstances
Used to stop instances
TerminateInstances
Used to terminate instances from the UI or automated if we find unresponsive redline13 load agent
4. Click “Review Policy”
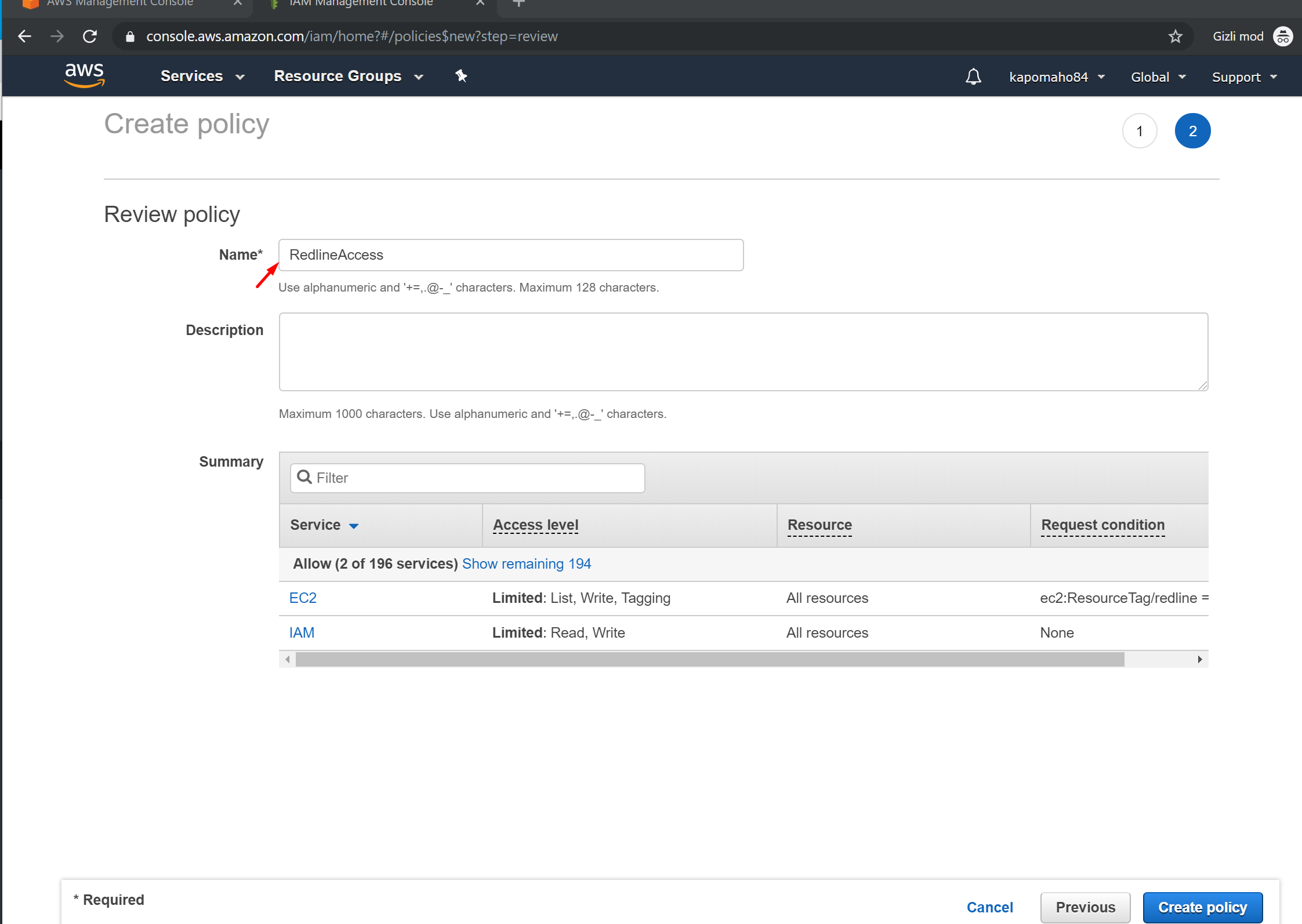
5. Enter a policy name (e.g. “RedlineAccess”). Optionally a description.
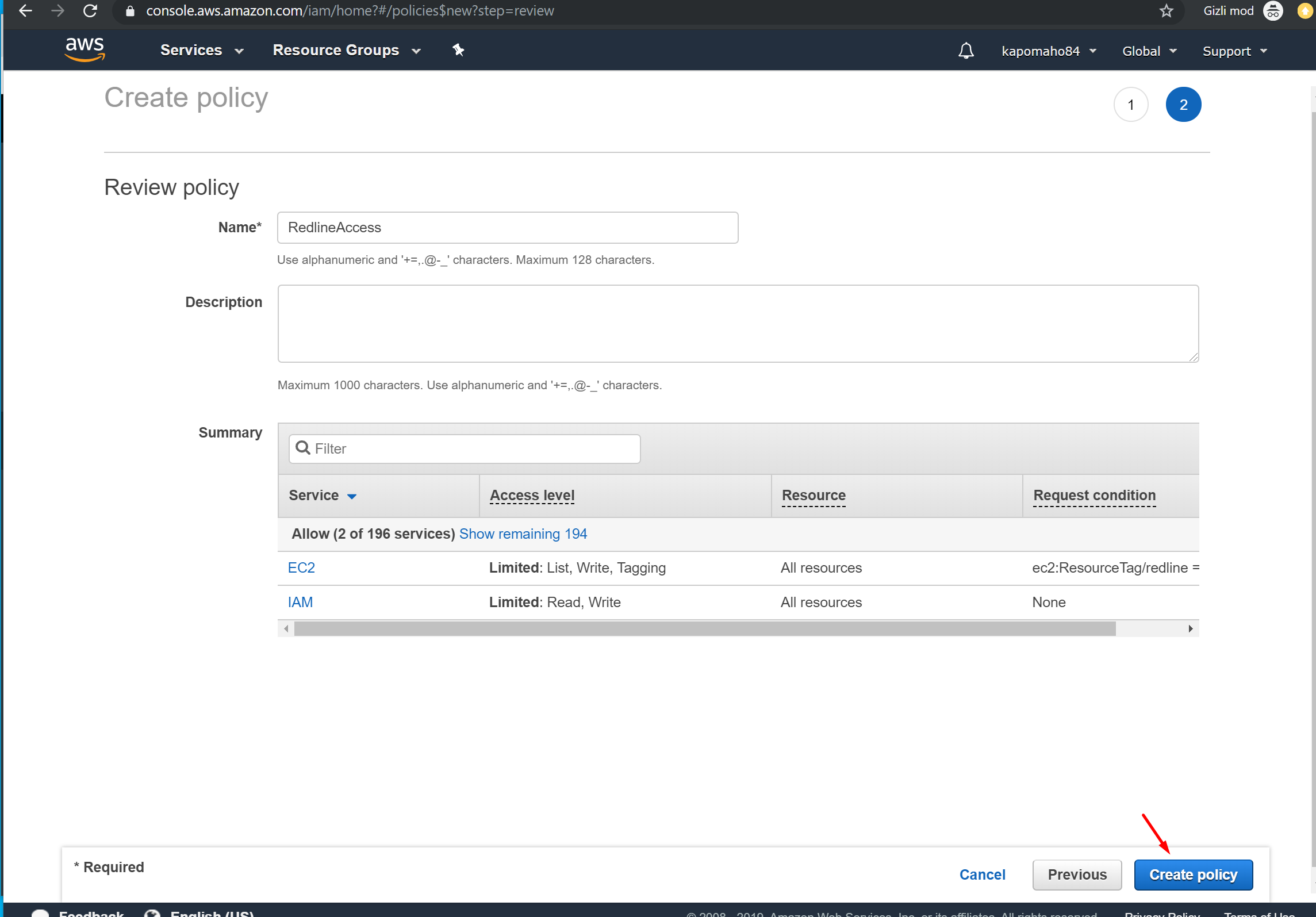
6. Click “Create Policy”. You should see ‘Policy Name’ has been created.
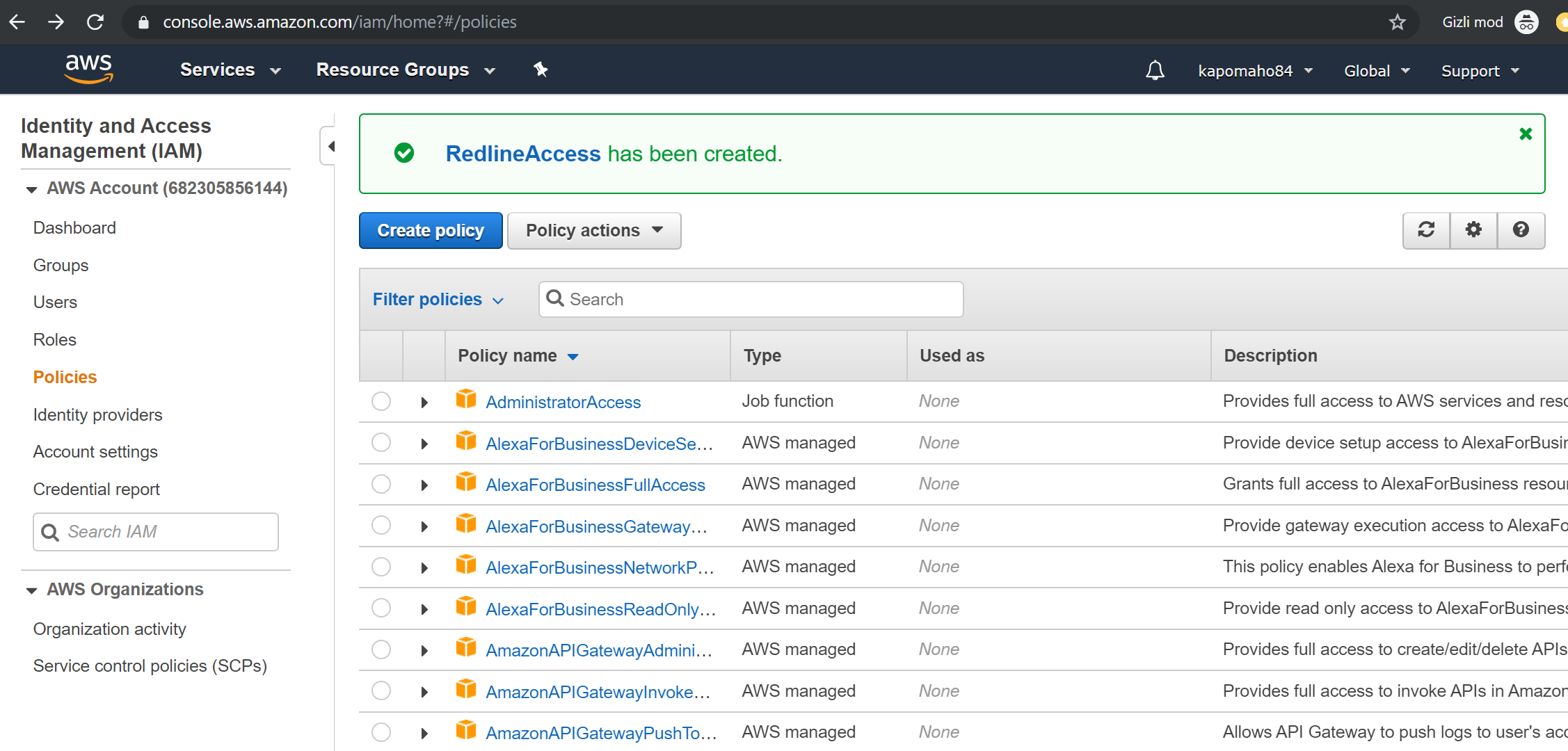
7. Click the “Roles” link, then the “Create Role” button.
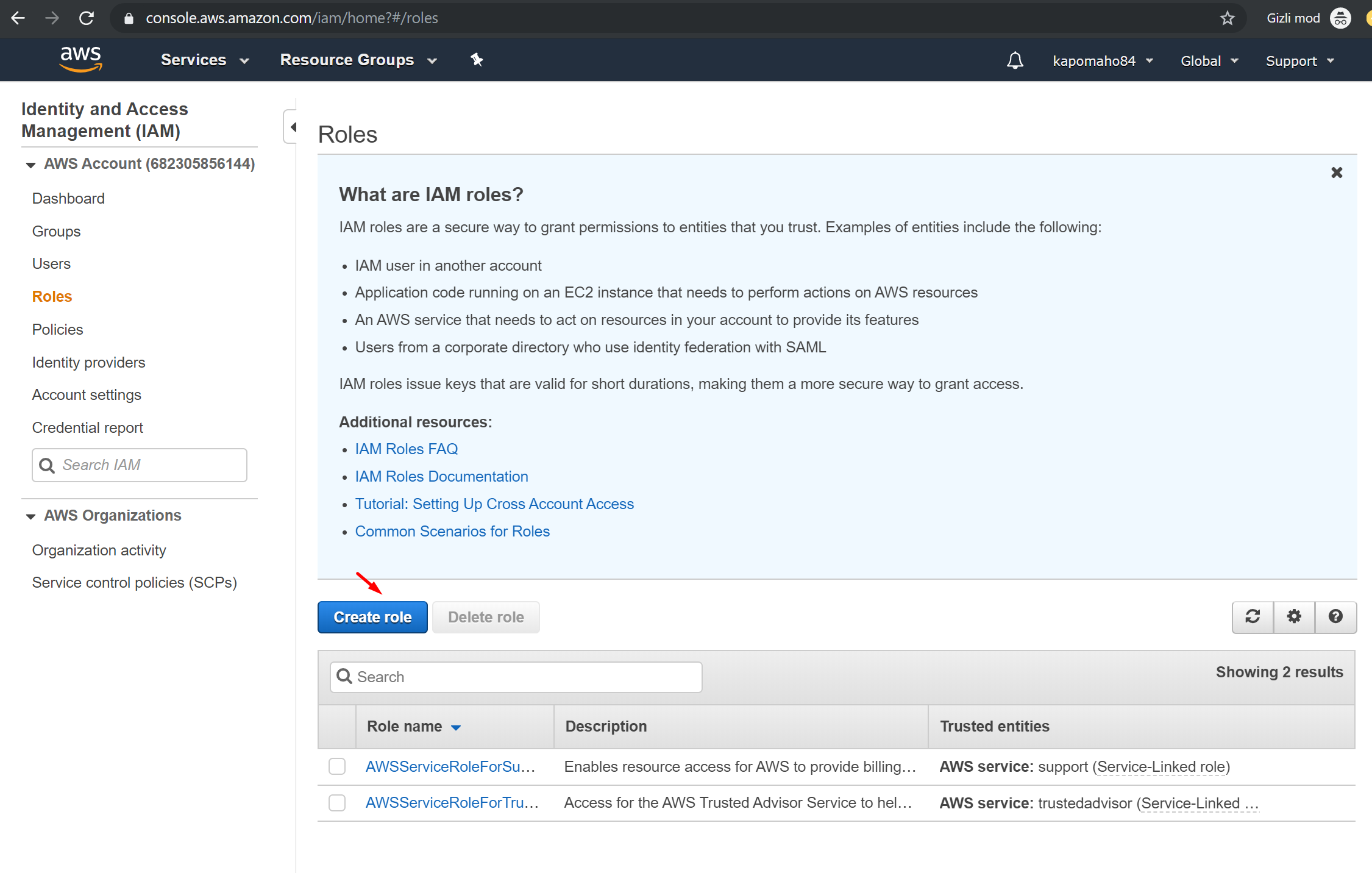
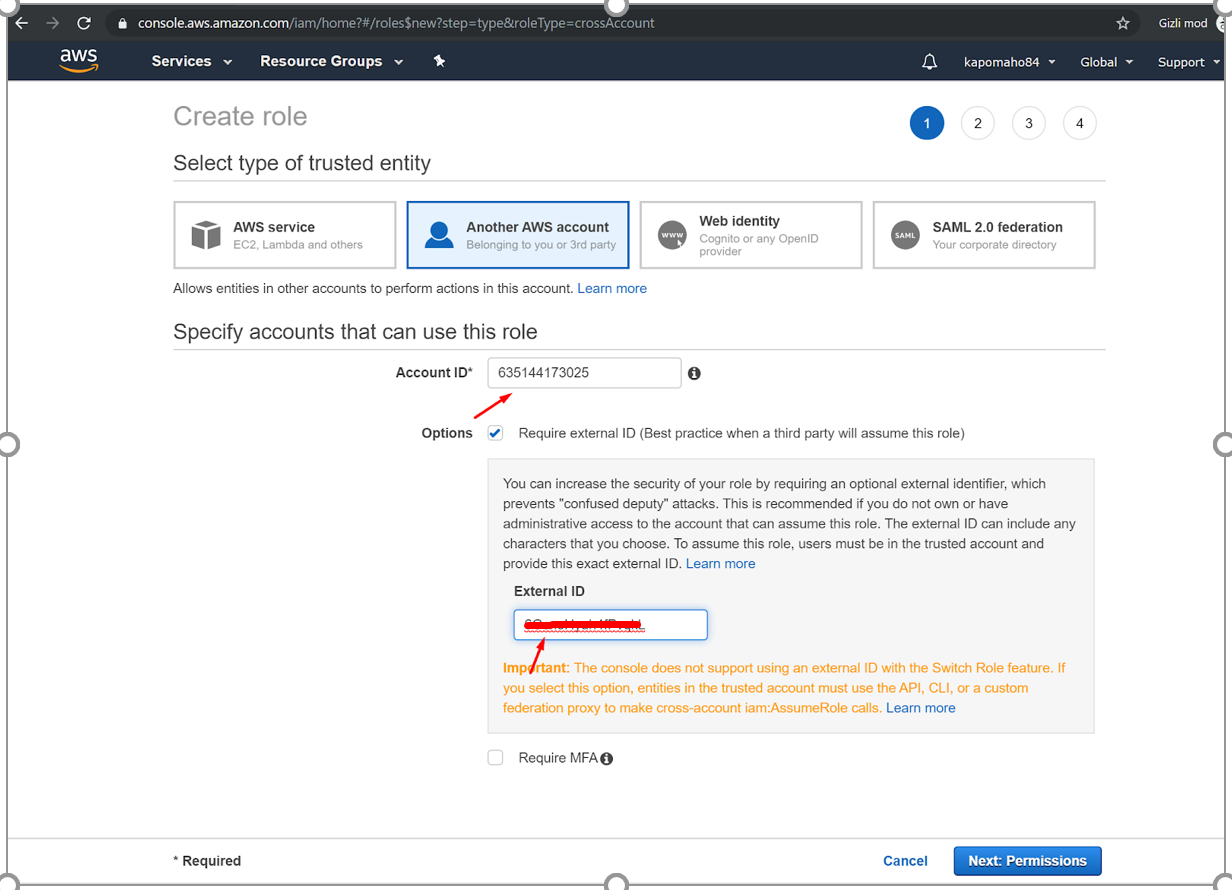
8. Select “Another AWS Account” option.
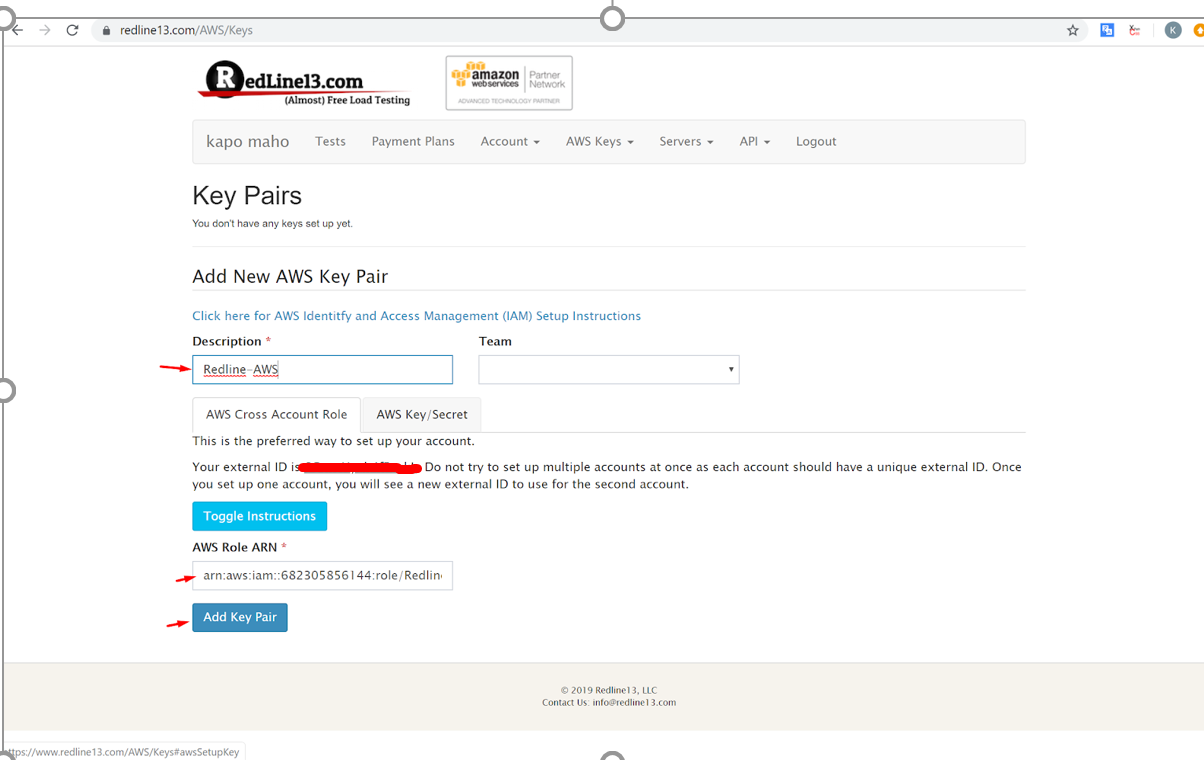
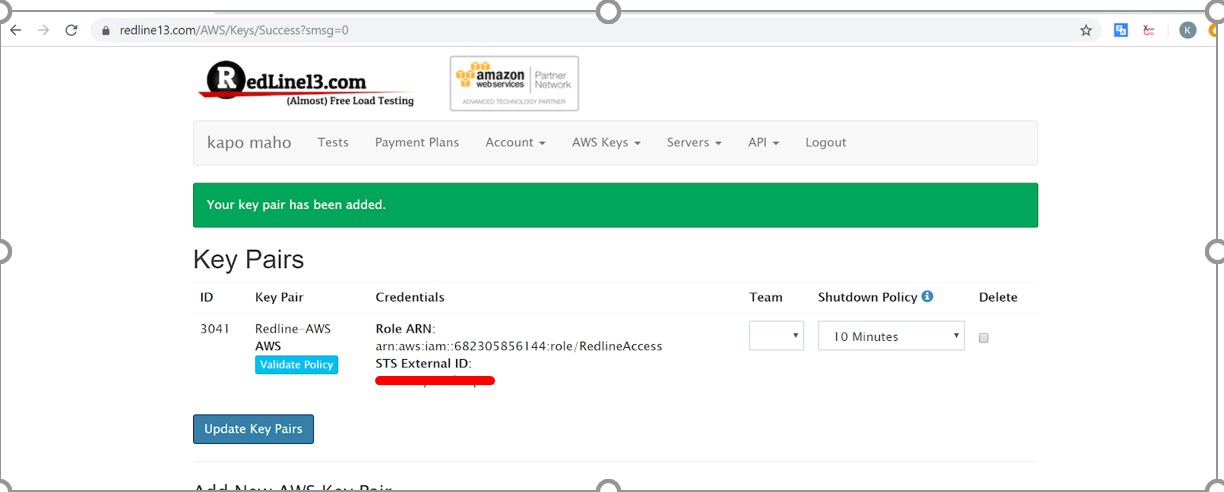
Enter Account ID, for example “635144173025”, check “Require external ID”, and enter the External ID listed on the RedLine13 account setup screen.
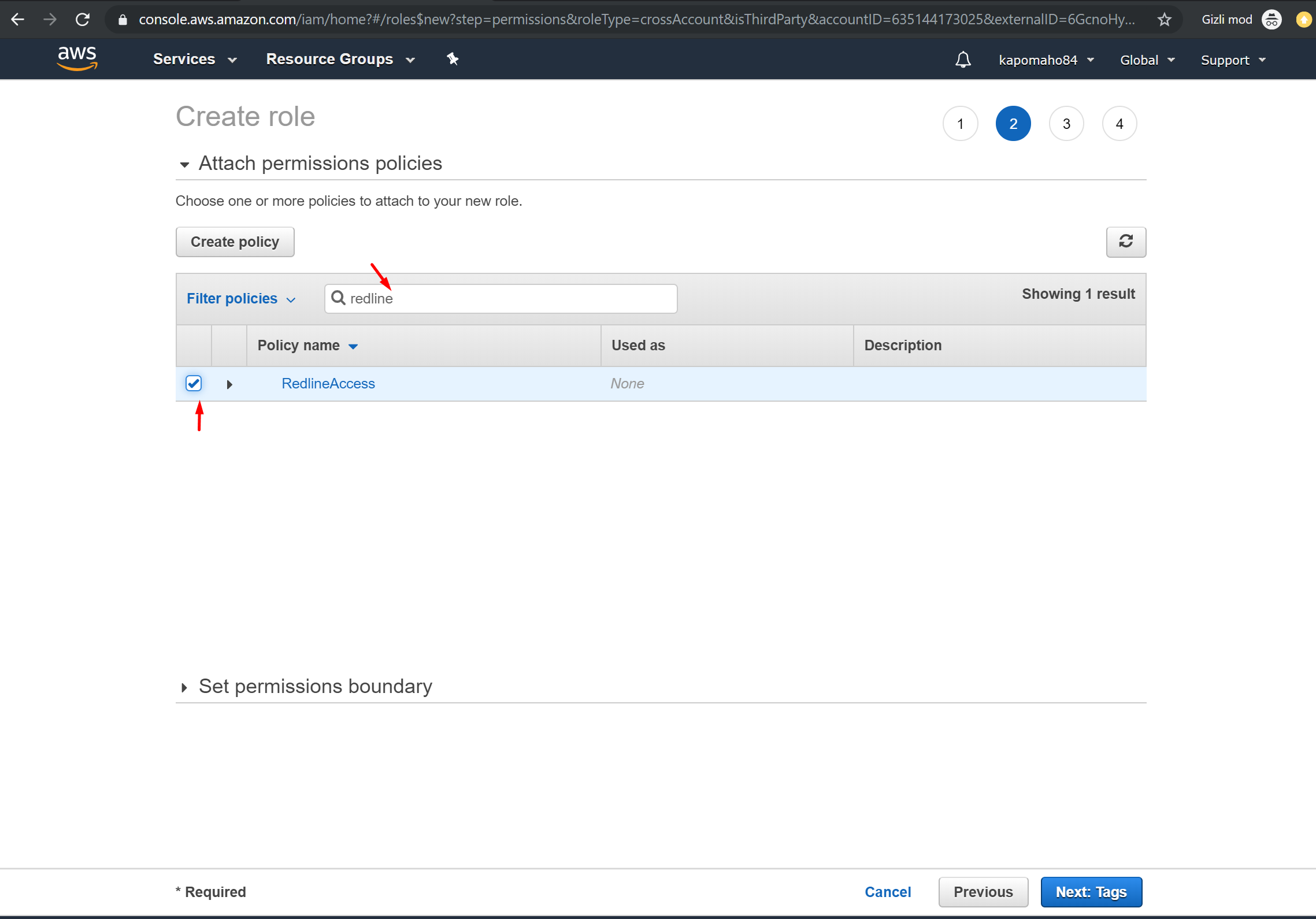
9. On the next step, Select the policy that you created above.
10. On the Review page, enter a Role Name (E.g. “RedlineAccess”), then click “Create Role”.
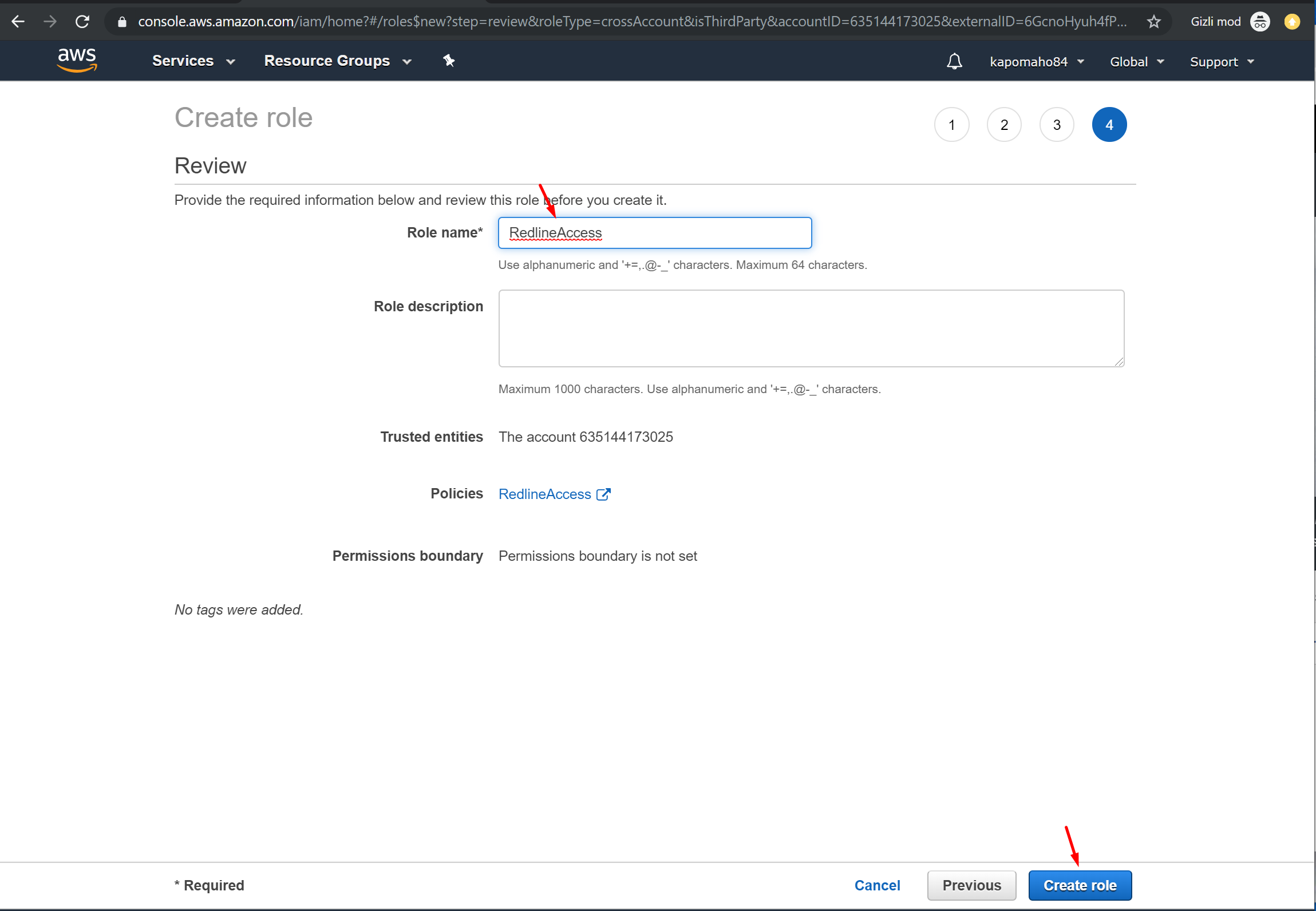
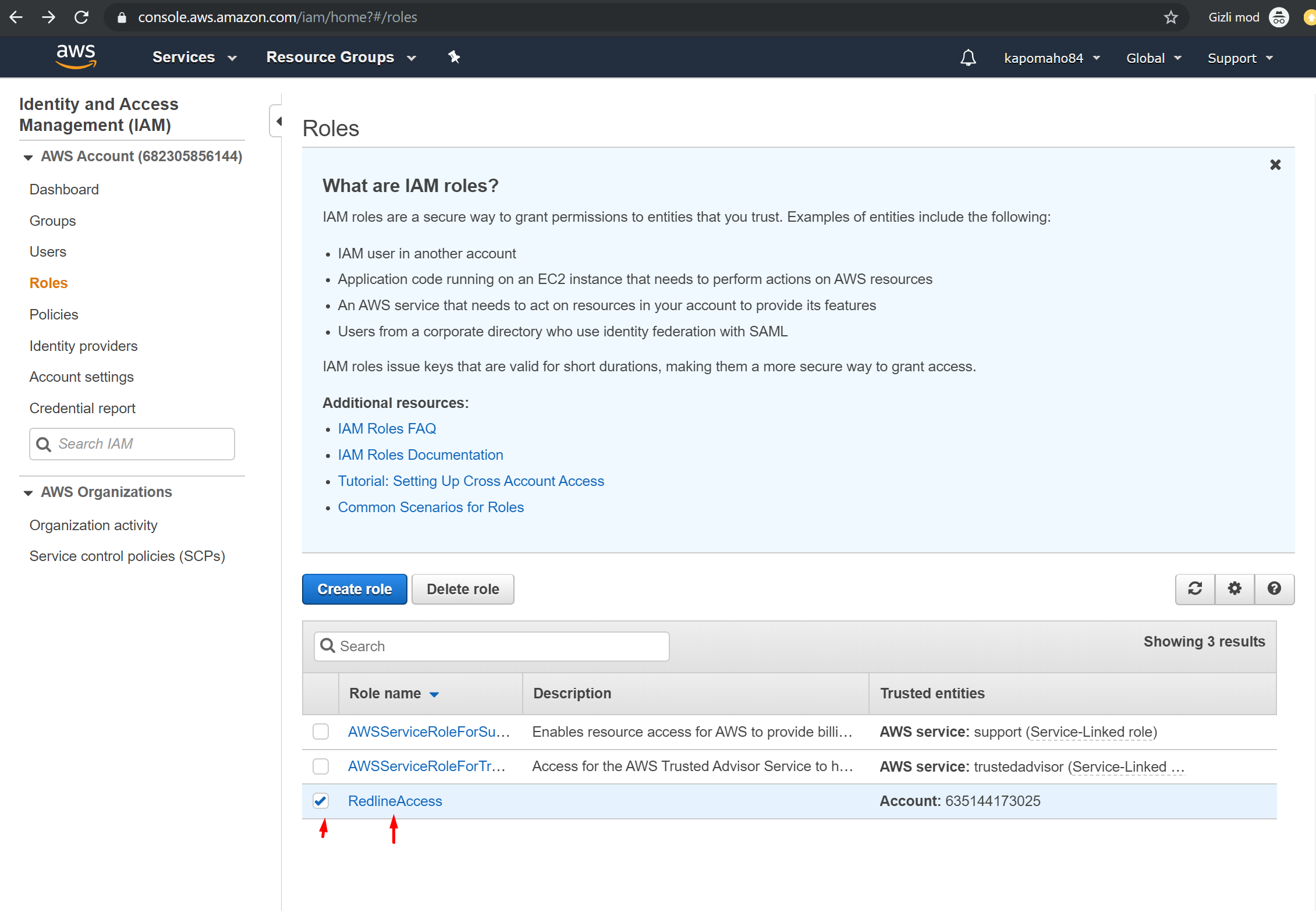
11. On the roles page select (click into) your newly created role
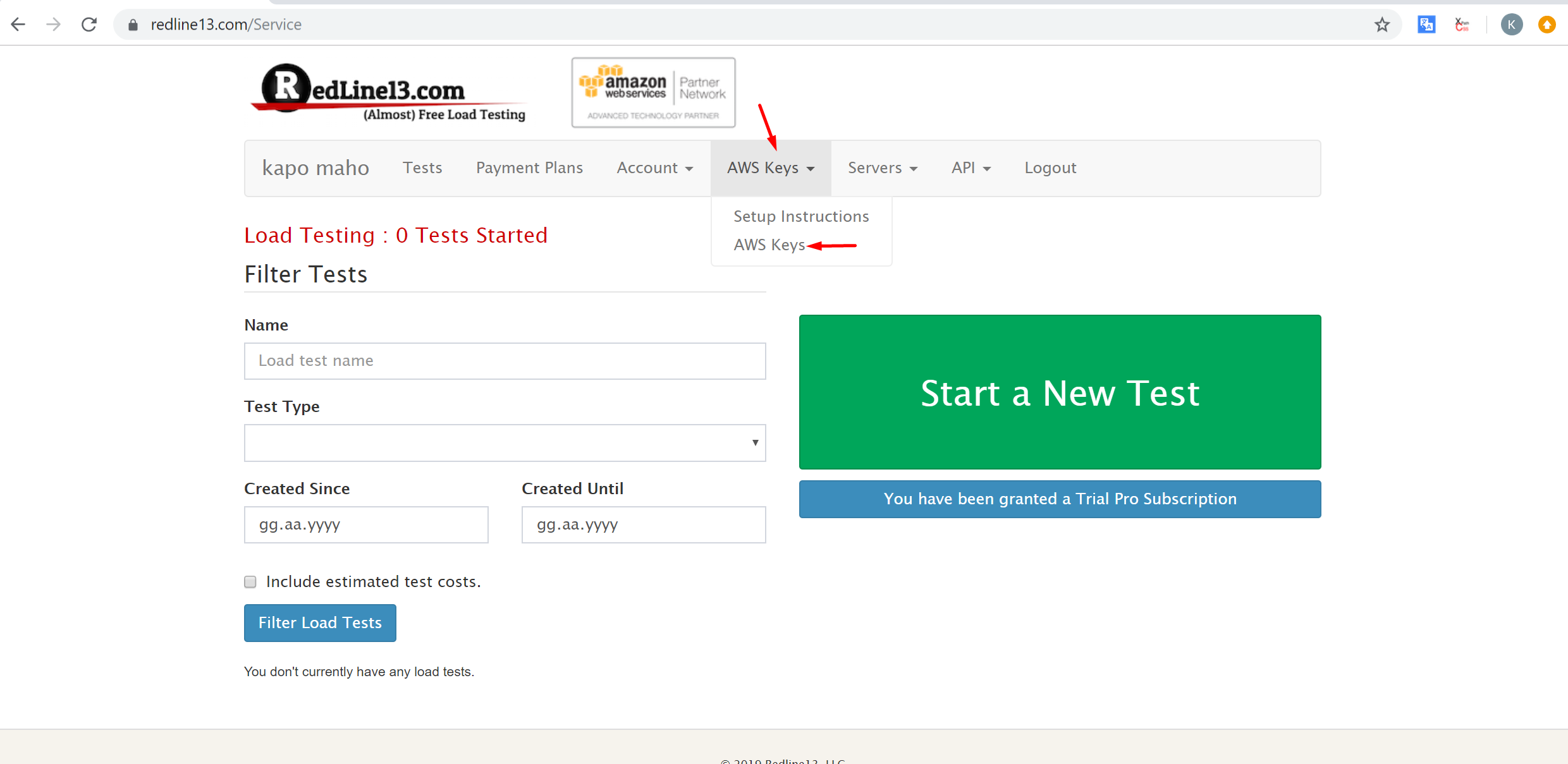
12. Switch back to Redline13 webpage and click AWS Keys->Aws Keys buttons
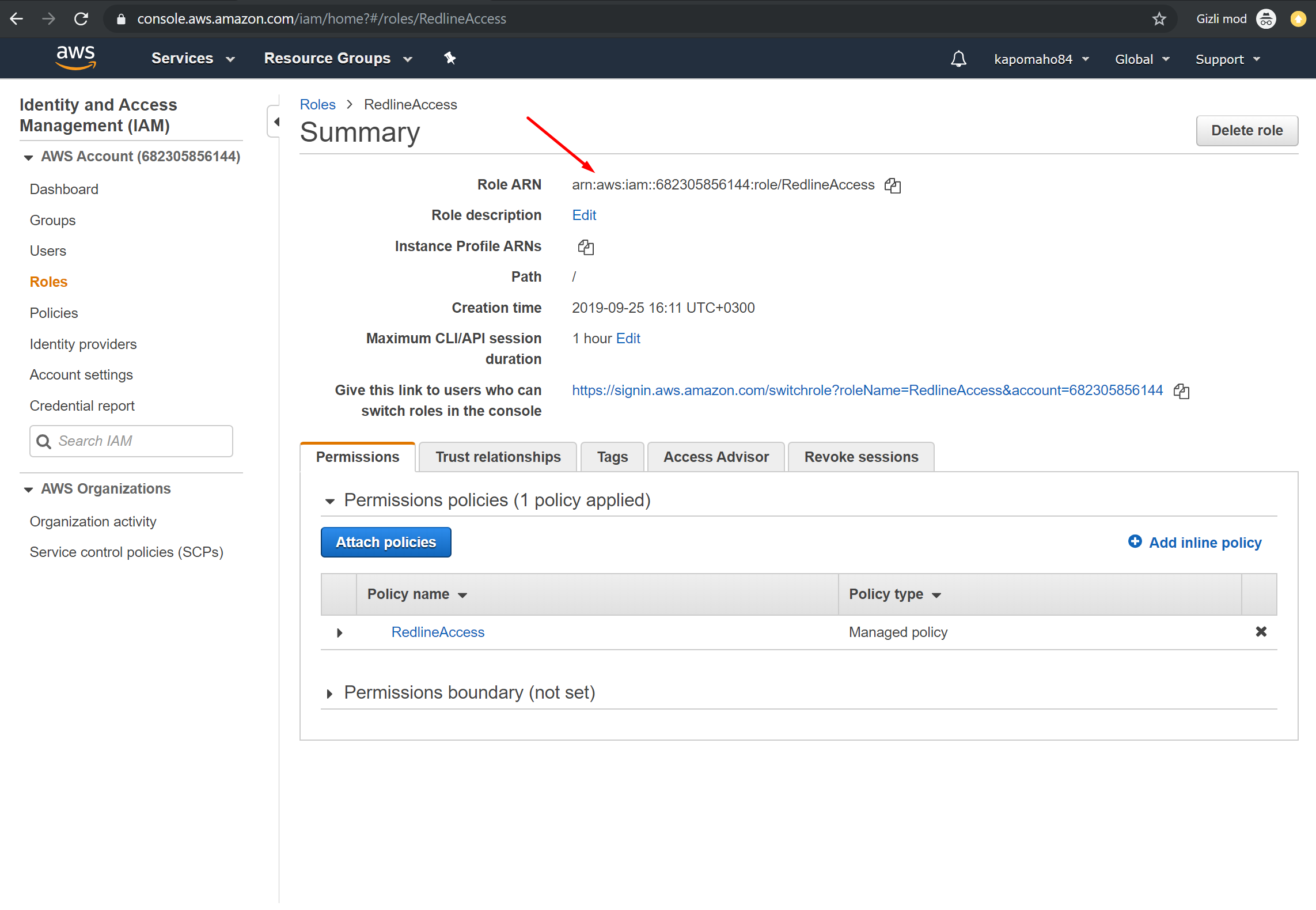
13. Copy the Role ARN and enter into the RedLine13 form, then submit the form. You’re done! Now you start using AWS for load testing with RedLine13.